Improve the security of your application. Gain more trust from your customers


2FA adds an additional layer of security to the authentication process
There are 3 major problems of the log in process




Emphasoft 2 FA solution is the choice of successful client applications!
Two Factor Authentication is a MUST for companies who deal with sensitive information
Two Factor Authentication has a lot of advantages
We offer: 2 approaches & 2 solutions
Fast and simple
Log in with a Google like solution
Your customers will verify using 3 digits google-like method to confirm their access. For applications
Customized and sophisticated
AWS amazon recognition API - based solution Access with Face recognition model.Available for applications as well as physical places.Your customers will get access to the application or device using face ID or special gesture
What we created for our client
Physical access to the place the premises authorised by face and gesture recognition System can identify persons, their age, and gender. It easily integrates with existing camera systems. Using the AI and Computer Vision technology, it can gather and analyze massive amounts of data.
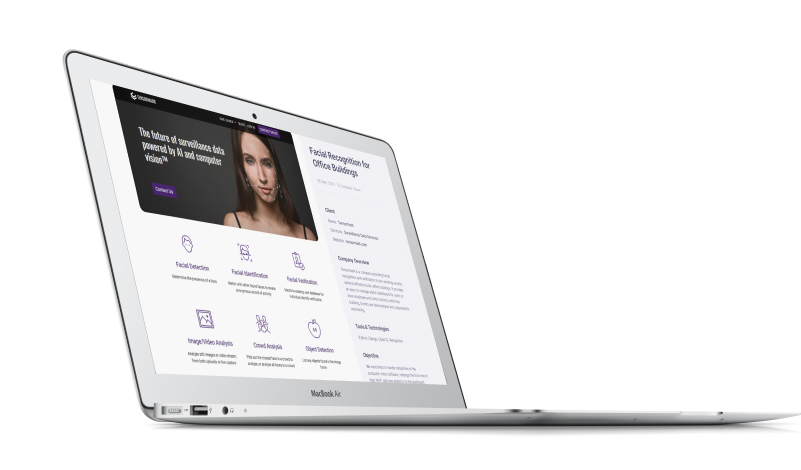
- Recognition dashboard
- Video 2-Factor Authorization (V2FA)
- iOS Chek-in App
Access to the crypto wallet, sending funds, creating reports authorised via face recognition to decrease user errors. Access to the wallet is authorized by gesture, transactions over $100 000 are authorised with face recognition to mitigate mistakes.
- Recognition dashboard
- Facial 2-Factor Authorization (V2FA)
- Gesture 2-Factor Authorization
Authorization in local directory of a bank branch with local 2FA application Bank with over 30 000 employees did not want to use any third party 2FA applications. Bank CEO wanted to have their own secure 2FA application for the employees. This solution increased security levels and helped prevent non-employees from gaining access to the local server containing sensitive and confidential data.

- Private access to 2FA application
- Integration with local security infrastructure
- Security dashboard with data about time and numbers of authorisations by each employee monitored by the security office



 Schedule a Discovery Call
Schedule a Discovery Call Schedule Call
Schedule Call